Encryption is becoming a big deal these days and some of the top companies are implementing it for their customers. Somewhat leading the pack is Google, which is focusing on Gmail. But others, such as Skype, have been encrypting video and voice chats for some time. Clearly this is a good thing for users.

However, there are a myriad of problems surrounding the use of encryption, especially in the case of public carriers like Skype, Google, Microsoft and others. And the issue is becoming a growing problem as cloud base storage systems and so-called secure email services claim to employ encryption to protect users.
The first thing to understand is that most commercial encryption systems have servers that act as pass-through transactors for email, video conferencing and the like. When an email, or Skype call is processed on one of these servers, the message is decrypted and then re-encrypted if the recipient of the message or video call is encrypting. If the recipient is not using encryption, then the message is generally sent in the clear to the recipient. To give an example, Google has been using a type of secure transaction based on what is called Transport Layer Security or TLS. If you are downloading email through the Gmail system (even from other accounts you own), during the set up phase you will be asked if your alternative email service uses TLS.
TLS is a mediocre form of security, but it is absolutely no security on the Google server itself. There are commercial and "other" reasons why this is so.
Google's Gmail makes its money by scanning emails and pushing advertising and promotions to its Gmail users, generally through the Google Chrome browser. This is a very big business. The online ad market is estimated to be worth $25 billion annually, and some experts, including Google's top display-ad executive, Neal Mohan thinks the market will grow to as much as $200 billion. Google employs more than 100 executives to support the scan and advertise business. It is not something Google can afford to abandon, and of course, Google is not doing that.
A second reason Google and most other providers are not encrypting traffic that transits their servers. is the government. All these companies --Google, Yahoo, Microsoft to name a few, depend on the government for their very survival. Thus while they may, for public consumption, be willing to jump up and down and say how much they value privacy and abhor government interventions, they all cooperate with the government. This means responding promptly to both court orders and so-called National Security Letters requesting access to certain accounts. This reaches even further than just National Security and can likely include many government-led investigations for crime fighting, and even more worrisome, "crime fighting" that is really political maneuvering. We still have a lot of learn from the IRS scandal and the so-called missing emails.
What is true of Google is likewise true of Skype. Government access to Skype was confirmed in leaked top secret documents obtained by Edward Snowden and made public by Glenn Greenwald. In the NSA's Prism program, one document shows how the Skype server stores information and how Prism can access it.
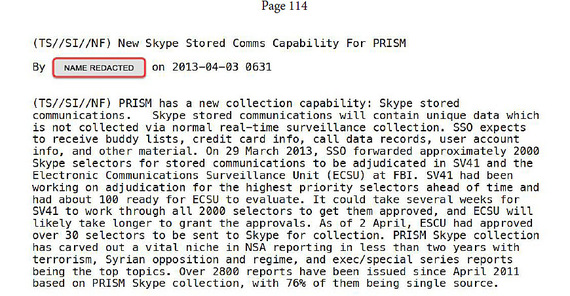
Again, the issue is that whatever transacts into the Skype server is there for the taking.
Servers, therefore, are the primary issue not only because they enable lawful spying to protect national security, but the servers can be targeted by hostile governments, criminals and "ordinary" hackers.
Typically a server should be housed in a truly secure location and should be managed by people who are not security risks. No major company today claims that it has in any way vetted its employees to guard against theft of data at the server, and even if they made the claim, it is far from clear they have a ways and means to go about handling such a problem. In the government itself, only people who work on classified servers require vetting and such vetting involves careful background checks including any criminal record or convictions. Even the government method fails: largely because the government outsources this work to third parties who are in it for the money, not necessarily providing hard core assessments. Edward Snowden was "cleared."
Private companies cannot rely on the FBI, CIA or any other government agency for help in checking out employees. They need to use private companies to try and assist, but this is time consuming and expensive, and often the work is poor. Private commercial servers are quite understandably highly vulnerable to "insider" attacks. Some foreign governments are known to have planted people in many top companies just for this reason.
Servers can also be hacked from the outside through the Internet. Government servers experience hack attacks thousands of times every day on its servers. So do companies in the critical infrastructure, such as Defense and Aerospace firms and energy companies. And companies in the competitive space are often hit by cyber attacks to steal vital proprietary information. The matter is made infinitely worse if public providers such as Gmail and Skype, and many others, are used routinely by company employees.
Encryption is only successful when the server is in the control of the enterprise and the enterprise has sound security policies that cover both its fixed network and its mobile communications. Many, if not all, so-called secure mobile phones are run from servers controlled by unknown persons, often in third countries where no one can say what the security situation really is, who is behind the organization, and what recourse a user has if he or she is compromised. A third party man in the middle is a very big risk. The risk grows greater when the provider is offshore and cannot be reached through reasonable lawful means.
Here is a recommendation: the best servers are servers controlled by the enterprise or organization, provided the organizations or enterprise implements prudent security and strong oversight of its operations. The use of commercial services is a bad idea for protecting corporate and government information and should be avoided at all costs.
No comments:
Post a Comment